AWS SSM / Session Manager support in WinSCP
I'm trying to hook up WinSCP and AWS SSM / Session Manager. But I cannot get it to work with current tooling... :(
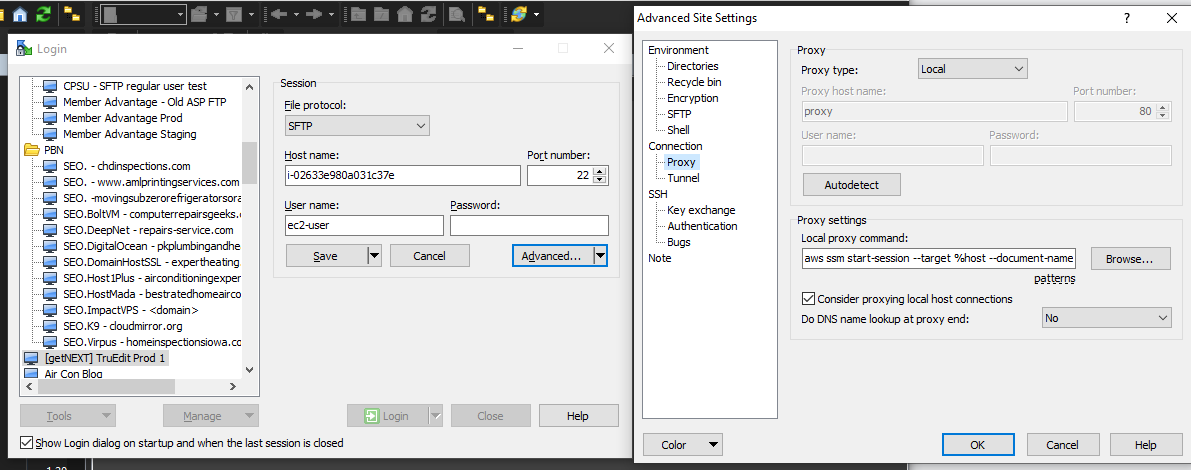
My attempt was to use Advanced > Proxy. Specify proxy as local and use the following proxy command:
But it appears as if WinSCP doesn't even get to that stage as it first looks for host (which is an AWS instance ID, not a valid host normally ie
AWS SSM would normally recommend to use
Any help would be appreciated or if native support for this feature was added in, that'd be great :)
My attempt was to use Advanced > Proxy. Specify proxy as local and use the following proxy command:
aws ssm start-session --target %host --document-name AWS-StartSSHSession --parameters 'portNumber=%port' --profile getnext --region us-east-1
But it appears as if WinSCP doesn't even get to that stage as it first looks for host (which is an AWS instance ID, not a valid host normally ie
i-02633e980a031c37f.
AWS SSM would normally recommend to use
.ssh/config with the following config:
host i-* mi-* ProxyCommand C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe "aws ssm start-session --target %h --document-name AWS-StartSSHSession --parameters portNumber=%p"
Any help would be appreciated or if native support for this feature was added in, that'd be great :)